Root Cause Analysis Template
Overview
Now that you have completed your user research interviews, it is time to find the root cause. There are three parts to this activity. First, you will understand how to conduct a Root Cause Analysis by reviewing the Five Whys for Root Cause Analysis in your resource folder. Then you will review a sample Root Cause Analysis from other districts. Lastly, your team will conduct a root cause analysis using the Root Cause Analysis Template in your resource folder.
Part 1: Understand how to conduct a Use Cause Analysis
Root cause analysis is a structured team process that assists in identifying underlying factors or causes of an event, such as an adverse event or near-miss. Understanding the contributing factors or causes of a system failure can help develop actions that sustain corrections.
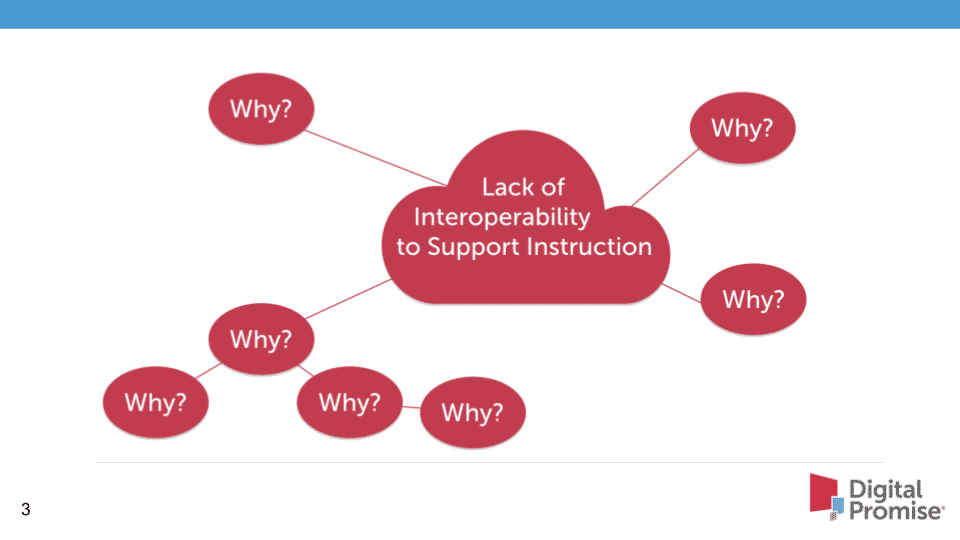
The Five Whys:
The Five Whys is a simple problem-solving technique that helps get to the root of a problem quickly. The Five Whys strategy involves looking at any problem and drilling down by asking: “Why?” or “What caused this problem?” While you want clear and concise answers, you want to avoid answers that are too simple and overlook important details. Typically, the answer to the first “why” should prompt another “why.” The answer to the second “why” will prompt another and so on, hence the name Five Whys.

Review this template labeled The Five Whys for Root Cause Analysis in your resource folder.
Part 2: Sample Root Cause Analysis
Review Assessment Data Root Cause Analysis examples below from other districts. Later reflect on which data interoperability pain points are the result of your district’s root causes.
Assessment Data Root Cause Analysis Examples
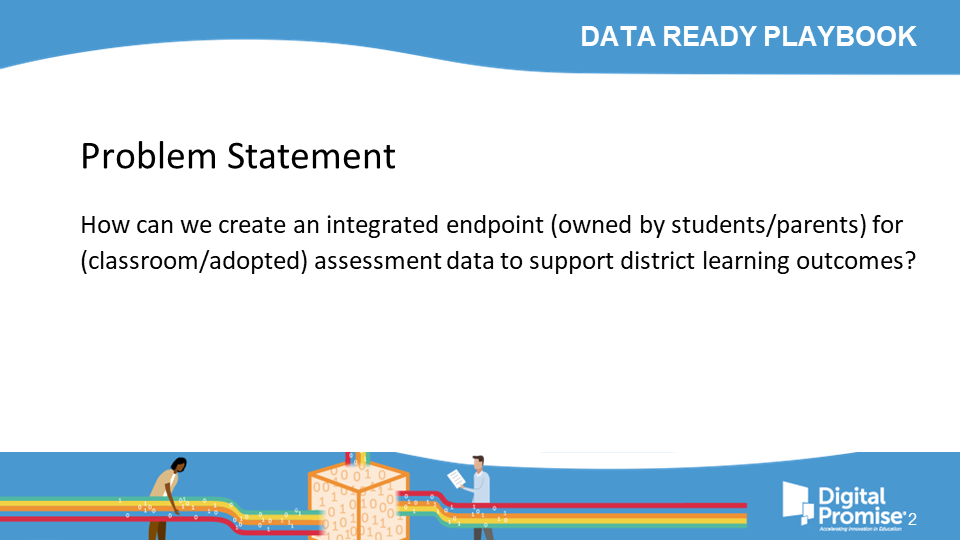
Problem Statement
Slide 3
District A
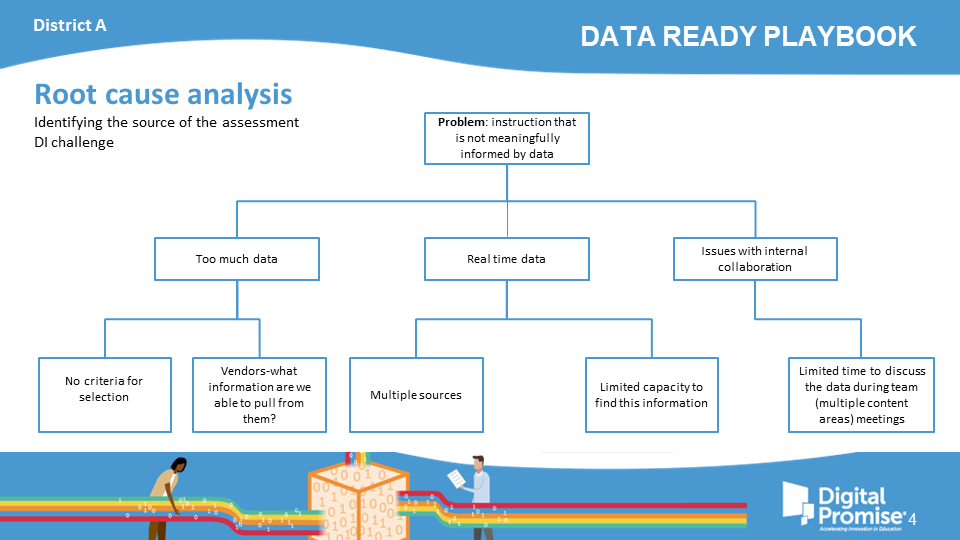
Identifying the source of the assessment DI challenge
District B
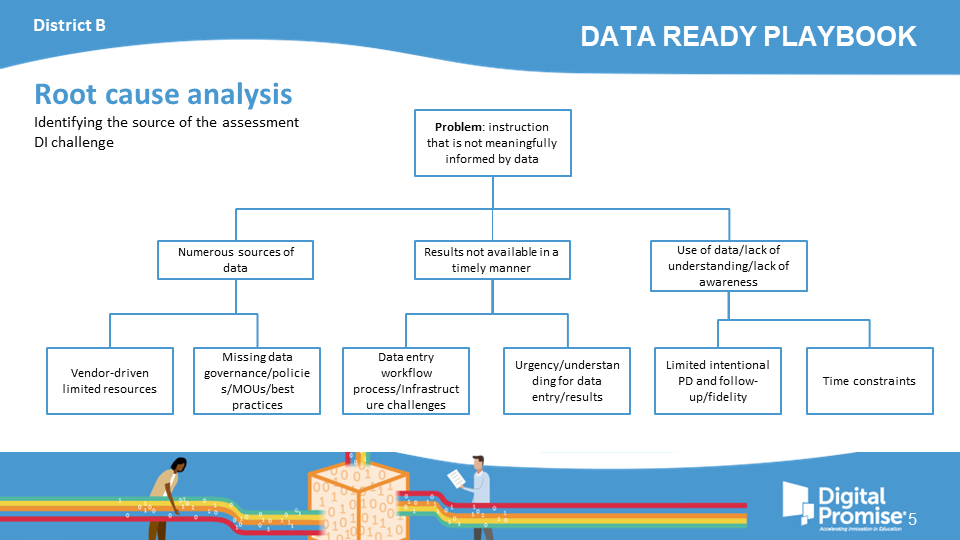
Identifying the source of the assessment DI challenge
District C
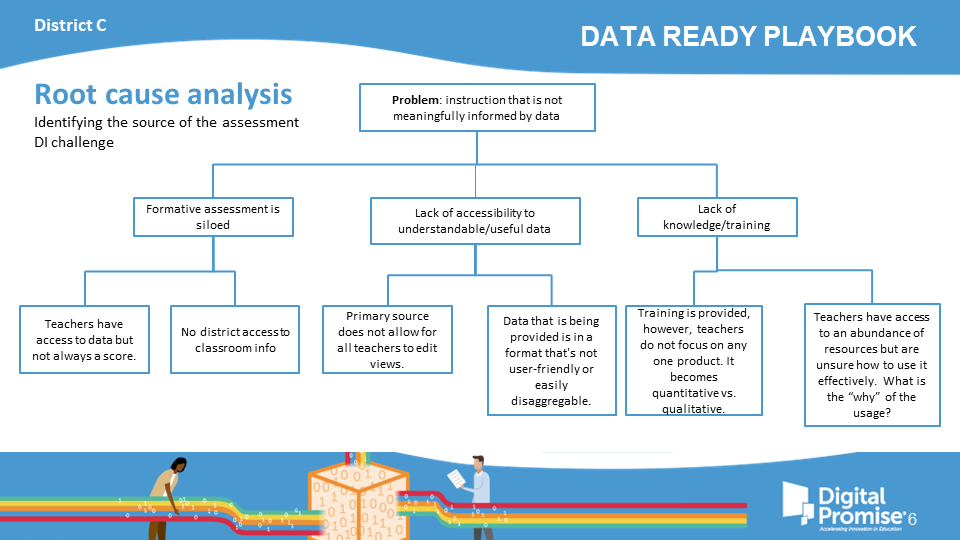
Identifying the source of the assessment DI challenge
District D
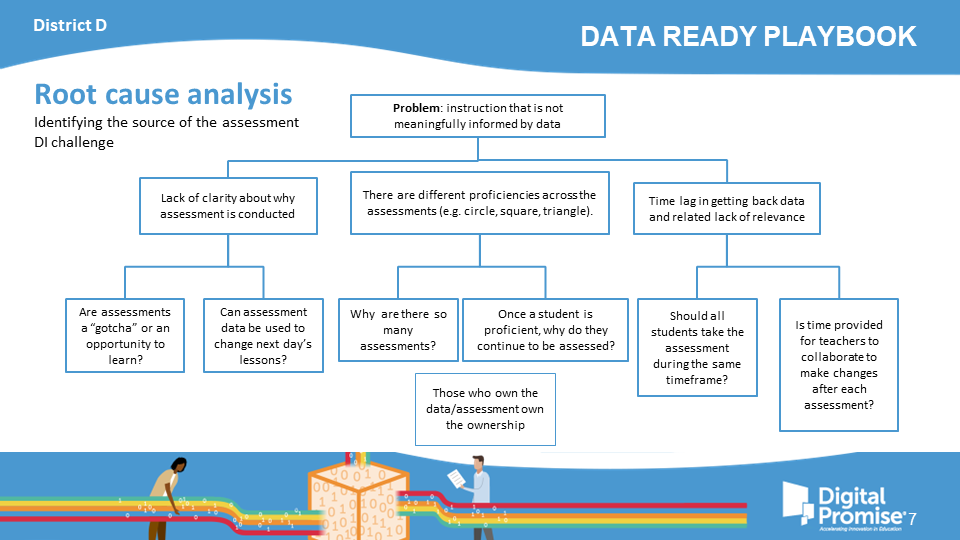
Identifying the source of the assessment DI challenge
District E
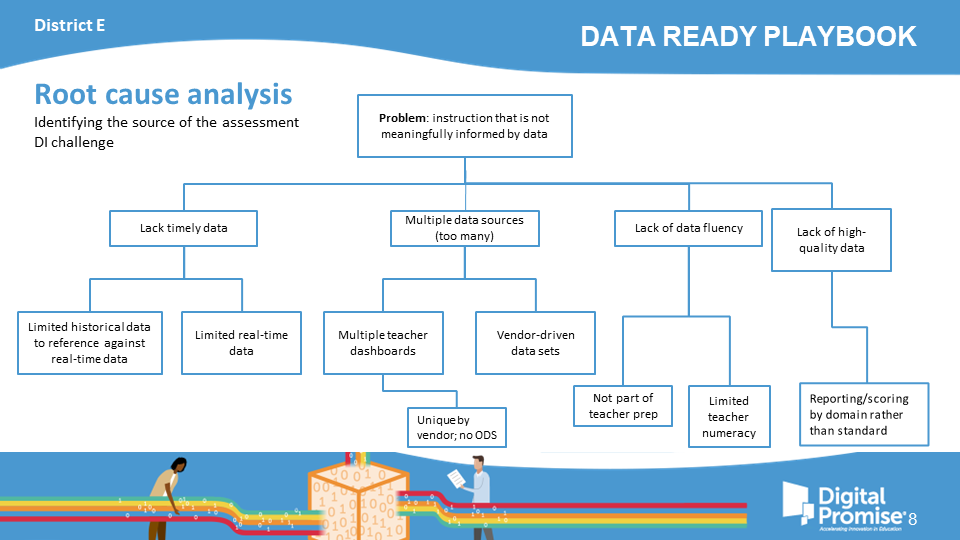
Identifying the source of the assessment DI challenge
Summary
Though all the sample districts have the same problem statement, each district found unique root causes to the problem
Part 3: Conduct a Root Cause Analysis

Locate the Root Cause Analysis Template 2.0 in your resources folder. Conduct a root cause analysis of perceived challenges using this template.
List of Data-Related Pain Points
- Limited documentation on existing systems and integrations
- Difficulty planning for recent or upcoming system changes
- Future systems integrations into the Ed-Fi architecture
- Process to get vendors to use APIs to connect the data between systems, this includes existing vendors and the procurement process for new vendors
- Coordination with various system administrators can be difficult
- Decisions made to increase interoperability can mean a sacrifice in the granularity local values provide
- Descriptors may need to be different depending on operational context
- Systems within the same education organization have different code sets and can be time consuming to align these though Data Mapping
- Poor data quality introduces blockers during the development phase.
- Insufficient policies for granting systems access
- Lack of process to request data
- Lack of confidence causes sign-off hesitancy
- Metrics are shared without ensuring the audience has a clear understanding of what they represent
- Difficulty deciding the correct permissions for and access for different user roles
- The interpretation of a specific metric can vary across departments
- The way a metric is calculated differs across department
- When mapping codes, it can be difficult to determine what code should be given to a record when definitions are not clear.
- Staff across the organization has different understandings of the requirements and mapping
- Unclear user permissions processes and policies
- No formal process for granting system access
- Lack of consideration of student privacy requirements (FERPA), such as n-counts